Acoustic Coupler
Contents
Mechanism
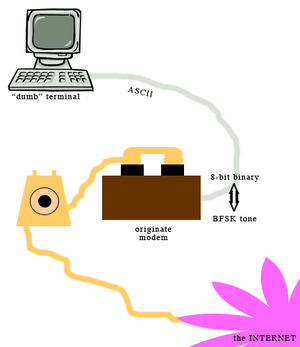
The acoustic coupler is one component in a larger system of connectivity using telephony to transmit data between two computers. The coupler sits atop a modem that both emits and receives tones from the interconnected computers, encodes and decodes those tones to and from binary, and then passes bits of data to a software program installed on the user’s computer which processes the binary data into human-readable information.The earliest modems communicated at a baud rate of 300 bits per second (bps), transmitting information encoded as auditory signals using Frequency Shift Keying. In this method, a different tone corresponds to individual bytes of information. Modems employ Binary Frequency Shift Keying (BFSK), in which there are only two bytes transmitted: 1, or the “mark,” and 0, or the “space”. Frequencies are overlaid onto a carrier wave, and the change in frequency denotes either a mark or a space.
In order for a modem to both transmit data from the originate modem (linked to the user’s computer) and receive data from the answer modem (linked to a remote computer, hosting, for example, a bulletin board system), the acoustic coupling modem must achieve duplex capability, thus being able to discern the mark and space frequencies of both parties. In a duplex system, the originate modem transmits data encoded in an auditory tone of 1270hz for the mark and 1070hz for the space frequency. The answer modem transmits tones at 2225hz for the mark and 2025hz for the space frequency. These universal frequencies are determined by the tone-generating capability of the prevailing telephone hardware.
Early models, like the 1964 Livermore Model A, consisted of a wooden box encasing a cradle for the telephone’s mouthpiece and earpiece, ringed with rubber. This cradle sits atop the device’s modem, built from analog circuitry, to generate tones of a certain frequency. Early acoustic modems also included a Schmitt trigger—a simple circuit that compares electrical input to a certain threshold, and outputs a binary reading, “high” or “low,” accordingly. The box would also necessarily include a serial port connector for communication with the computer or terminal controlled by the user.
Geneology
This simple notion, where the different combinations of binary data, of “on” and “off,” and its attendant mapping of “on” and “off” to auditory frequencies, is not novel. Despite the revolutionary potential presented by the internet, the underlying mechanism by which data is transmitted via modem is a remediation of the telegraph. The modem joins the family of devices that "involved sound in the process of inscription." (Gitelman, 216) Furthermore, the device itself is a stand-in for the telephone's end user, the human itself.
The First Phreak
The acoustic coupler’s physical and aesthetic design is a direct product of the prevailing political and economic conditions regarding telephony at the time of the device’s conception. Until 1956, telephone companies controlled the consumer’s telephone use from end to end: not only were the phone lines owned exclusively by the company, phones in each building were rented to the consumer (at a fee included in the recurring service charge), and were physically hardwired into the electrical infrastructure of the building. It was both illegal, and physically inconvenient to interrupt this system of transmission with any product not issued by the phone company. The first modems were thus built to circumvent the restrictions imposed by the political organizational structure of telephony, and the very design reflects this resistance. The modem interrupts the system of telephony at the only point where it is legally and technically possible—at the point where the human would normally stand in to hear and speak—and therefore creates a system where two computers are “talking” to one another in a language borrowing heavily from the telegraph. This decision to mimic the human act of conversation, a decision made out of necessity to find an exploit in the political enclosure enforced by the telephone industry, left an indelible impact on telecommunications infrastructure. Although modems have evolved over the past decades, the logic of transmission measured in binary bits per second remains unchallenged.
The earliest devices are exceedingly simple to understand, and the boxes were built to be easily taken apart for maintenance. This accessibility reinforces the ethos of the culture that uses the device: participants of “modem culture” are encouraged to find their own way through the system using their curiosity as guide. It is a culture that supposes a certain amount of taking-apart and putting-together-again in order to achieve a desired result. At its essence, the invention of the acoustic coupling modem was the first “phreak” (a type of hack directed towards the telephone system). This imbues the device with a certain revolutionary ethos that is deeply entwined in its design.
New Methods of Inscription and the Hacker Mythology
Although the acoustic coupling modem resisted the “black box” design, the attendant method by which data was encoded and decoded by the terminal or computer fostered a contrasting mythos of computing culture that hinged upon the obfuscation of the reading and writing process. Sound is played into the device, and sound is generated and emanates from the device. However, this sound is translated into and from data by a hidden mathematic process of decoding tones into corresponding bit values.
To encode a typed letter into the appropriate tone, the key pressed must be interpreted by the terminal as an ASCII vaule. This value, which ranges from 1 to 255, is then translated into 8-bit binary, breaking down the 1 to 255 number into an 8-digit sequence of ones and zeros. Each digit is then played over the telephone at its corresponding frequency and carried over the telephone line to a “listening” computer at a remote location. To decode, the process runs in reverse. The modem must detect the answering computer’s tones as 8-digit sequences of binary data, then translate the chunks (bytes) into the correct ASCII characters which are then displayed on the user’s monitor.
The modem required that the process of inscription be obfuscated by several distict technological layers. The first layer is the typewritten process, mediated by the keyboard (although this layer of obfuscation had been introduced with the advent of the typewriter). The next layer was the electric conversion of ASCII values into 8-bit binary and then into the appropriate BFSK tone. Re-imagining the process of inscription as an electronic event, governed by mathematical logic served to mythologize computer use as an act that went beyond automatic writing: the advent of modem use introduced a new character onto the scene— the computer itself, which was to be anthropomorphized.
The rate of transmission, 300 bps, plays a key role in the process of anthropomorphism: faster than the human faculty to calculate data or read output, yet not fast enough to fully hide the process of calculation from the user, words “reveal” themselves on screen, character by character, as they are output. The experience of seeing the remote computer “talk back” to the user further encourages the anthropomorphization of the computer as an independant, humanoid entity. Not only do two computers “talk” to one another in a miasmic language of whirring generated tones, the user witnesses the decoding process as it unfolds, as if entirely perpetrated by a ghost in the machine. This ghostly visualization of automatically decoding characters into human-readable language has been turned into a boilerplate cinematic motif; most films portraying early internet use show a user in front of a terminal, inputting commands into a terminal, and receiving after a dramatic delay, a response in the form of slowly emerging text. Such dramatizations, cribbed from real life, lend to the mythology of the computer hacker as one adept at holding a conversation with the machine.
What was “said” and what was “heard”
As the described mechanism relies upon a high level of acoustic fidelity, a secure connection can be interrupted by any extraneous noise in the area of operation. Thus the very same hindrances to successful interpersonal communication effect the communication between computers connected via the acoustic coupler. A sudden burst of loud noise, a room with a steady hum from a generator can disrupt transmissions. A device whose rubber cups are too wide to create a tight seal around the headset can create the ideal situation for audio to become contaminated by non-diegetic sound. That the acoustic coupling modem shares the same fallibility as the human ear introduces an interesting set of contradictions. The apparatus maintains a thick aura of impenetrability due to the way it obfuscates, mythologizes, and even fetishizes the reading and writing processes. However, its humanoid vulnerability reveals the object as something that can be exploited by the most familiar and mundane tactics. By tricking the machine into “hearing” something other than what was “said,” an enterprising hacker interrupts the mechanism, forcing the apparatus to submit to his desires. This method of purposefully distorting what was “said,” like the children’s game Telephone, has less in common with the materiality of technology than with the sociability of interpersonal communication. The acoustic coupling modem is a device that is equally vulnerable to electric disruption, physical sabotage, and social engineering. Thus a culture of telephony hacking, or “phreaking,” rose around the particular challenge to outsmart the apparatus at whatever level it could be accessed.
References
- Chadabe, Joel. Electric Sound, The Past and Promise of Electronic Music. Prentice Hall, 1996.
- Gitelman, Lisa. Scripts, Grooves, and Writing Machines. Stanford University Press, 1999.
- Mann, Hugh. "Accoustic Coupler" http://www.wrybread.com/WryRoad/gadgets/coupler.htm
- Sterling, Bruce. Hacker Crackdown. Bantam Press, 1993.